Adversary simulation attacks.
Control Pack v1.11 The next generation C2 Framework.

Our Pricing Options
Choose the tier option that is right for you:
Full license: Control Pack contains all the functionalities you need to mimic the tactics, techniques, and procedures of cyber adversaries. All platforms are supported: Windows, Linux, Unix, Minix, SCO, Solaris, OSX and you can even target mobile and web.
What's also included: A full license of Control Pack also includes access to monthly updates and technical support.
Delivery: Personal keys are delivered via email within 24 hours of purchase and linked to the email address used during the purchase.
Do you need a quotation? Email us
Refund Policy:
⦁ We do not issue refunds for our products once the order is confirmed and the product is digitally sent.
⦁ Please be aware that all issued licenses cannot be modified or sent to a different email address at any later stage.
⦁ We recommend contacting us for assistance if you experience any issues receiving or downloading our products.
Technical support for lifetime licenses is valid for a period of three years from the date of purchase. During this time frame, customers will receive assistance and guidance pertaining to the product's functionality, troubleshooting, and maintenance.
One-year license - Control Pack
€950
1 year - (1 user license)
Regular full license
- ✖ Discounted price
- ✔ Control Pack full license + updates.
- ✔ Phishing campaigns.
- ✔ Ransomware ( DLL-Based ) for Red Team operations.
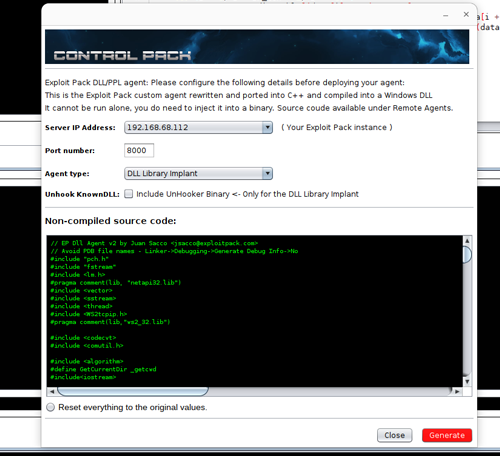
- ✔ DLL agent.
- ✔ .Net-Core agent.
- ✔ .Net Profiler agent.
- ✔ Python agent.
- ✔ In-memory agent.
- ✔ VBS-based agent (macros)
- ✔ Browser-based agent for XSS/Web attacks.
- ✔ WebKit-based ( Chrome ) plugin agent.
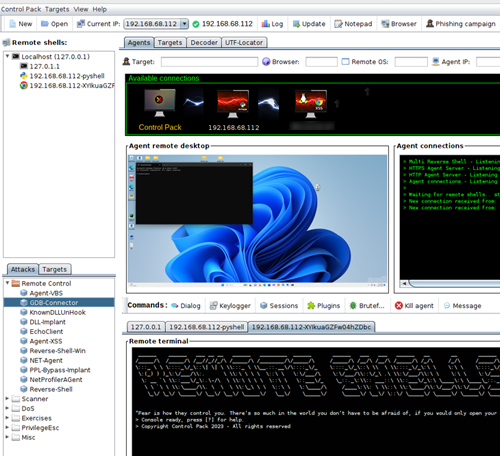
- ✔ Auto execution of commands for new connections.
- ✔ Simple reverse shells, scalable to full agents.
- ✔ KnownDLL unhook for evasion and AV bypasses.
- ✔ Protected Process Light ( PPL ) ready agent for AV bypass.
- ✔ Persistence methods.
- ✔ GDB Connector for debugging.
- ✔ IDA Pro Connector for debugging.
- ✔ Antireversing techniques for agent protection.
- ✔ Technical support.
1-year Control Pack + 1-year Exploit Pack
€1800
1 year - (1 user license)
Discounted price
- ✔ Discounted price
- ✔ Exploit Pack + Control Pack full licenses + updates.
- ✔ Phishing campaigns.
- ✔ Ransomware ( DLL-Based ) for Red Team operations.
- ✔ DLL agent.
- ✔ .Net-Core agent.
- ✔ .Net Profiler agent.
- ✔ Python agent.
- ✔ In-memory agent.
- ✔ VBS-based agent (macros)
- ✔ Browser-based agent for XSS/Web attacks.
- ✔ WebKit-based ( Chrome ) plugin agent.
- ✔ Auto execution of commands for new connections.
- ✔ Simple reverse shells, scalable to full agents.
- ✔ KnownDLL unhook for evasion and AV bypasses.
- ✔ Protected Process Light ( PPL ) ready agent for AV bypass.
- ✔ Persistence methods.
- ✔ GDB Connector for debugging.
- ✔ IDA Pro Connector for debugging.
- ✔ Antireversing techniques for agent protection.
- ✔ Technical support.
Take your adversary simulations and Red Team operations to the next level.
Control Pack has been designed to enable Red teams and cyber security professionals to simulate the attacks and tactics of a real threat inside and outside of an IT network. It has an easy-to-use graphical interface that will get you running in no time and customizable agents that can be tailored to your specific needs. Control Pack at its core is a commercial C2 that will allow you to conduct attack simulations with the added value of being capable to bypass the most current AVs and EDRs.
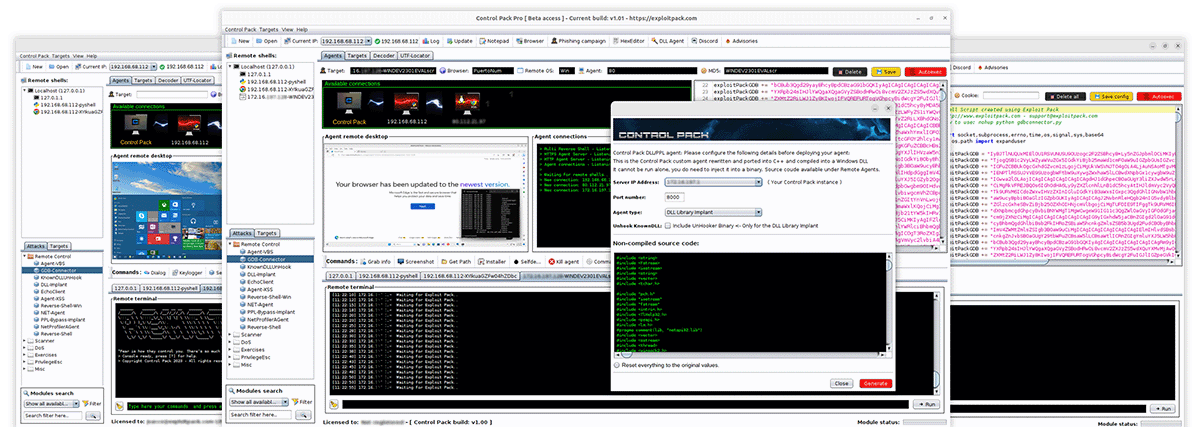
Browser pivoting
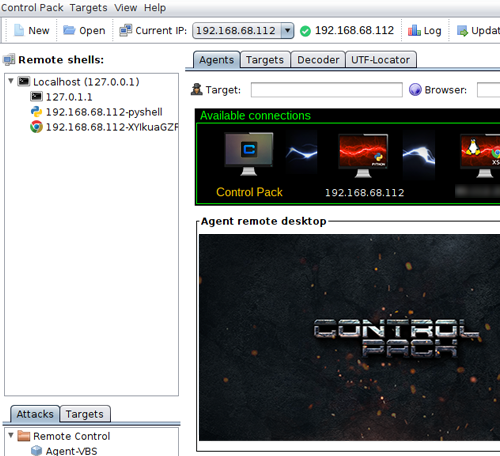
Make use of it to get around two-factor authentication, phishing campaigns and reconnaissance.
Covert communication
Obfuscate your communication to remain under the radar, switch between HTTP, HTTPS and Socket type of agents.
Reconnaissance and Post-exploitation
Discovers client-side software and version information that your target uses to identify potential known vulnerabilities. Make use of Control Pack agents to log keystrokes, take screenshots, download files, and execute other payloads.
Technical support and Training
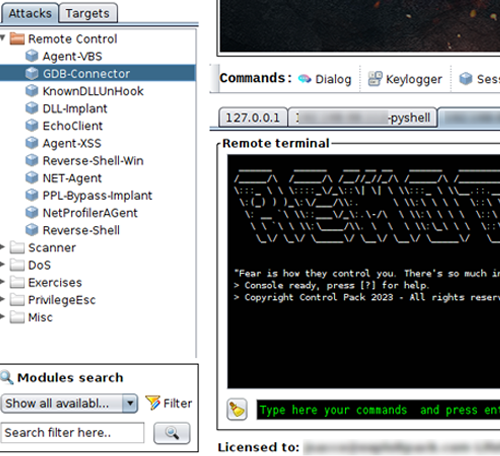
Never get stuck, your license includes technical support and consultation during your next project. We are here to help you achieve results and improve your Red Teaming capabilities.
Trusted by technical teams at companies of all sizes around the globe
What our clients say about Control Pack:
"Control Pack has been supporting our Cyber Security needs since the beginning. Their understanding of the relevance of staying current with the latest trends in attacks is crucial and their online training and technical support have definitely been an added value." - R. De Vries - Red Team Lead.