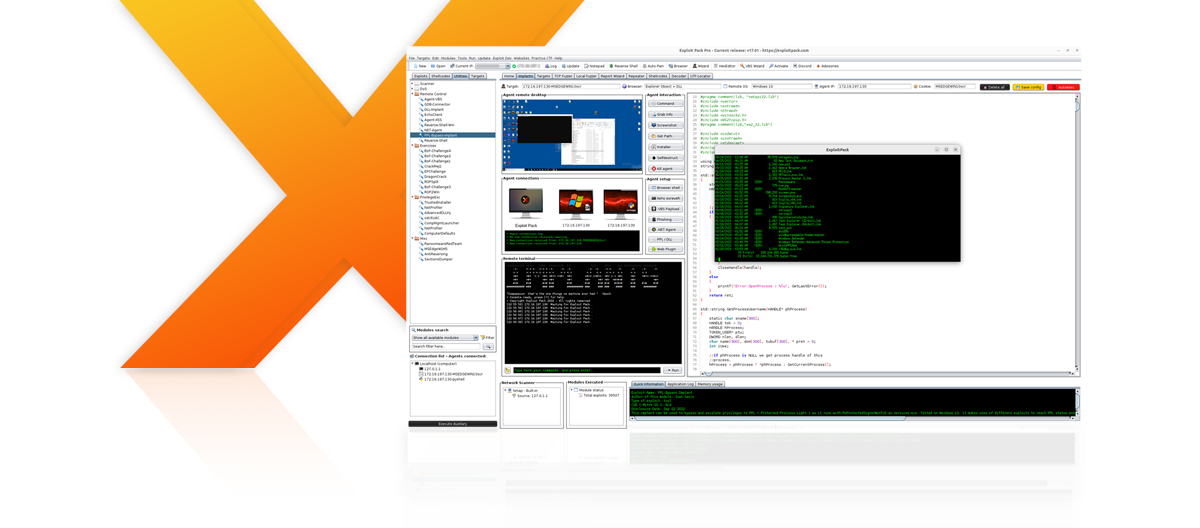
Exploit Pack full license: The real deal. Exploit Pack contains all the exploits you could possibly find out there: A set of 39.500+ exploits + Zero Days, Implants and post-exploitation modules. You can be sure that your next pentest will become unstoppable with Exploit Pack in your arsenal of tools. All platforms are supported: Windows, Linux, Unix, Minix, SCO, Solaris, OSX and you can even target mobile and web.
What's also included: A full license of Exploit Pack Framework also includes access to monthly updates, live online training and technical support for one or two years depending on the chosen license.
Control Pack full license: Control Pack contains all the functionalities you need to mimic the tactics, techniques, and procedures of cyber adversaries. All platforms are supported: Windows, Linux, Unix, Minix, SCO, Solaris, OSX and you can even target mobile and web.
What's also included: A full license also includes access to monthly updates and technical support.
Delivery: Personal keys are delivered via email within 24 hours of purchase and linked to the email address used during the purchase.
Do you need a quotation? Email us
⦁ We do not issue refunds for our products once the order is confirmed and the product is digitally sent.
⦁ Please be aware that all issued licenses cannot be modified or sent to a different email address at any later stage.
⦁ We recommend contacting us for assistance if you experience any issues receiving or downloading our products.
Technical support for lifetime licenses is valid for a period of three years from the date of purchase. During this time frame, customers will receive assistance and guidance pertaining to the product's functionality, troubleshooting, and maintenance.
One-year license - Control Pack
€950
1 year - (1 user license)
Regular full license
- ✔ Control Pack full + updates
- ✔ Phishing campaigns
- ✔ Ransomware ( DLL-Based ) for Red Team operations
- ✔ DLL agent
- ✔ .Net-Core and profiler agent
- ✔ Python agent
- ✔ In-memory agent
- ✔ VBS-based agent (macros)
- ✔ Browser-based agent for XSS/Web attacks
- ✔ WebKit-based ( Chrome ) plugin agent
- ✔ Auto exec commands
- ✔ Simple reverse shells, scalable to full agents
- ✔ KnownDLL unhook for evasion and AV bypasses
- ✔ Protected Process Light ( PPL ) ready agent for AV bypass
- ✔ Persistence methods
- ✔ IDA Pro and GDB Connector for debugging
- ✔ Antireversing techniques for agent protection
- ✔ Training and Tech support
Order Control Pack
One-year license - Exploit Pack
€950
1 year - (1 user license)
Regular full license
- ✔ Exploit Pack full license
- ✔ Monthly updates
- ✔ Over 39.500 exploits
- ✔ Zero day exploits
- ✔ Monthly Zero day exploits from our lab along with video tutorials
- ✔ Exploit editor ( reconfigure, modify and add new exploits )
- ✔ Exploit Finder (by OS, type, service, etc.)
- ✔ Local Fuzzer
- ✔ Remote Fuzzer
- ✔ Web attacks
- ✔ Post-Exploitation
- ✔ Remote control
- ✔ Automated attacks
- ✔ Network scanner
- ✔ Targets management
- ✔ Hexa editor
- ✔ Reverse shells ( include a custom shellcode or convert into an executable file )
- ✔ Live online training
- ✔ Technical support
Order Exploit Pack