Our latest technical articles
-

WDK 10.0.26100.0 GDT for Ghidra 12
WDK 10.0.26100.0 GDT for Ghidra 12 using clang preprocessing and sanitization so Ghidra’s parser accepts all kernel/CRT prototypes. Coming from IDA Pro that does this automatically, in Ghidra is not...
WDK 10.0.26100.0 GDT for Ghidra 12
WDK 10.0.26100.0 GDT for Ghidra 12 using clang preprocessing and sanitization so Ghidra’s parser accepts all kernel/CRT prototypes. Coming from IDA Pro that does this automatically, in Ghidra is not...
-
![[Video] Juan Sacco, founder of Exploit Pack at No Hat conference (Italy)](//www.exploitpack.com/cdn/shop/articles/Screenshot_2025-12-22_173719_845038cb-29e2-49e4-a01a-52b0b00d4240.png?v=1766421604&width=533)
[Video] Juan Sacco, founder of Exploit Pack at ...
Juan Sacco from Exploit Pack delivered a focused, hands-on workshop titled “Subverting the Windows Kernel with rootkits and exploits” at No Hat in Italy. The workshop focused on three primary exploit...
[Video] Juan Sacco, founder of Exploit Pack at ...
Juan Sacco from Exploit Pack delivered a focused, hands-on workshop titled “Subverting the Windows Kernel with rootkits and exploits” at No Hat in Italy. The workshop focused on three primary exploit...
-
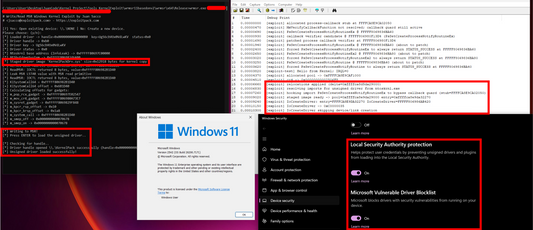
Unsigned drivers loading on Windows 11 25H2 (fu...
After having developed working exploits for physical r/w (ZwMapViewOfSection) and r/w through MSR (L_STAR) for Windows 11 25H2, I decided it was time to take it up a notch and...
Unsigned drivers loading on Windows 11 25H2 (fu...
After having developed working exploits for physical r/w (ZwMapViewOfSection) and r/w through MSR (L_STAR) for Windows 11 25H2, I decided it was time to take it up a notch and...
The offensive security toolkit, ready to order:
-
Exploit Pack
Regular price From €1.200 EURRegular price€1.200 EURSale price From €1.200 EUR -
Control Pack
Regular price From €1.200 EURRegular price€1.200 EURSale price From €1.200 EUR -
Kernel Pack
Regular price From €1.200 EURRegular price€1.200 EURSale price From €1.200 EUR -
Ultimate Pack + Discount
Regular price €3.400 EURRegular price€3.600 EURSale price €3.400 EURSale

The next generation exploit framework
Exploit Pack: The offensive exploitation framework
Exploit Pack is an exploitation framework for exploit developers and penetration testers. A massive library of 39,500+ exploits and monthly 0-days at your disposal.
It includes a robust set of tools for payload generation, post-exploitation, and automation, making it a core component for offensive security red teams.

The quietest C2. Undetected by AVs and EDRs.
Control Pack: Userland C2 with undetected agents
Control Pack is a userland Command-and-Control (C2) framework built for professional Red Teams and security researchers.
It’s designed to simulate advanced adversary techniques in realistic corporate environments. Control Pack includes multi-platform agents and incorporates the latest techniques to mimic stealthy attacker behaviors.

Kernel Exploitation Framework
Kernel Pack: Kernel access C2 framework
Kernel Pack is our Command-and-Control (C2) with Kernel-Level access. It's the only tool of this type in the market that allows you to configure, interact, setup and deploy your own rootkit (software driver).
Kernel-Level process hiding, disable monitoring and sensors, EWT and AMSI and much more.
Who is behind Exploit Pack, Control Pack and Kernel Pack tools
We are a specialized, research-driven cybersecurity company based in Maastricht, in the southern Netherlands. Our team focuses on advancing knowledge in digital security while developing innovative solutions to help organizations anticipate, detect, and defend against emerging cyber threats. With a strong commitment to research excellence, we combine academic knowledge with practical expertise to deliver robust security strategies.
Our tools help penetration testers, red teams, and cybersecurity professionals across different industries, giving offensive teams what they need when ‘standard tools’ hit a wall.
We develop to push further, dig deeper, and deliver results that other tools can’t. That’s why professionals around the world keep our offensive tools in their arsenal.

Frequently Asked Questions
Is there a trial version?
The trial versions of our tools are available for download here.
The trial versions of EP, CP, and KP are designed to give you a first look at how our tools work. They install without activation and don’t expire, but they are not full-featured products. Certain capabilities are intentionally limited to prevent misuse and piracy.
If you need access to the complete set of features, you’ll need a licensed version.
What are your payment methods?
We accept debit, credit cards, PayPal payments, and bank transfers. We don’t accept cryptocurrency. If you prefer to make a bank transfer, you can directly place an order and select "Bank Deposit" during checkout or contact us.
Licensing and Multiple Users
All Exploit Pack products are sold as single-user licenses. Please make sure to order one license per user. If you require multiple licenses for your team or organisation, contact us and we’ll assist you with bulk licensing options.
I need a quote/invoice
Get in contact with us at support@exploitpack.com. Please include the company details and VAT number (if you're located in the EU).
Do I need a quote/invoice before ordering more than one license?
That is not necessary. You can select the number of licenses (up to 5) when you place the order. If you need more licenses for your team, please contact us at support@exploitpack.com.
Can I use the same license of Exploit Pack / Control Pack / Kernel Pack on multiple computers/systems?
Our tools are watermarked and single-user. Only one machine can use a license. In case you need to make changes, please get in contact with us. If you have multiple users, please order licenses accordingly.
Can I change the email linked to my Exploit Pack / Control Pack / Kernel Pack license?
Licenses are always linked to the email used during the purchase or provided at checkout. Once issued, this email cannot be changed. Lifetime licenses are permanently linked to the purchase email and are only for personal use.
I have purchased one of the tools. When will I receive the license?
Licenses are manually generated and may take from a few minutes to a few hours to be sent.
Update fails or the download is corrupt. What should I do?
Some included exploits might be flagged as malware. We recommend adding an exception in your antivirus or, ideally, running Exploit Pack inside a VM (e.g., VMware or Parallels). We do not recommend disabling your antivirus.
What do I need before installing Exploit Pack / Control Pack / Kernel Pack?
Before installing our tools, ensure that you have the latest version of JAVA JDK installed and an internet connection available.
For Windows: https://www.oracle.com/java/technologies/downloads/#jdk21-windows
For MacOS: https://www.oracle.com/java/technologies/downloads/#jdk21-mac
I am having issues opening Control Pack / Exploit Pack / Kernel Pack.
Usually, this is due to not having the correct Java JDK installed; double-check this first. Also, make sure to install the tools directly, and do not copy the folders from one system to another. All our products are watermarked, which may cause the tools to malfunction if copied. If you are still facing issues, please send us an email to support@exploitpack.com, run the program on a terminal using the command “java -jar ExploitPack.jar”, and please send us the log.
I am having issues with my key or need new credentials.
Please get in touch with us at support@exploitpack.com.
Is there documentation for the tools?
Yes, you can find the documentation for our tools here:
Exploit Pack: Documentation Exploit Pack
Control Pack: Documentation Control Pack
Kernel Pack: Documentation Kernel Pack





![[Video] Juan Sacco, founder of Exploit Pack at No Hat conference (Italy)](http://www.exploitpack.com/cdn/shop/articles/Screenshot_2025-12-22_173719_845038cb-29e2-49e4-a01a-52b0b00d4240.png?v=1766421604&width=533)




